- Sun 16 June 2024
- Public
- marci
- #Networking
Intro
I would like to block certain websites in the evening inside my home network for certain reasons. I also don't want to modify any settings on the client side (access may be limited - we have to use our epic networking skillz).
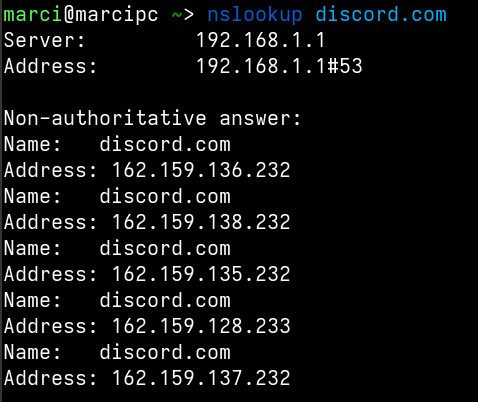
In this example I will take a look at Discord.
Obviously, there are 2 methods of blocking a site:
-
Using a DNS block list
- Automatically scheduling this using pfSense is a bit hard for wildcard addresses
- Static domains can be automatically resolved by pfSense and it will block every entry in the response. This proves to be very useful if a certain website uses domain level load-balancing.
-
Dropping packets to given IP addresses - We can obviously drop packets for given IP addresses.
We will use both methods for achieving the best possible results.
Collecting information
IPs
First, we need to know what to block. When a client is using the given website/service we can perform a packet capture on the network using pfSense's built-in functionality. We get a nice .pcap file which we can analyse using Wireshark.
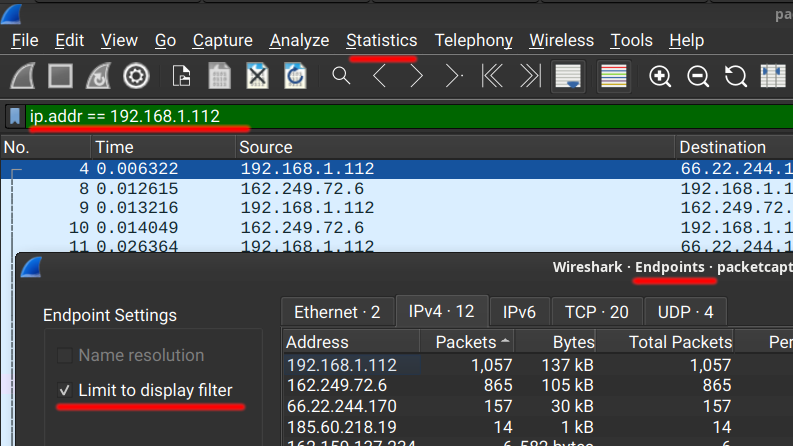
After loading up the capture file and setting some basic filters we can use the Statistics > Endpoints functionality in Wireshark to view the most used hosts.
Manally looking up the IPs and checking their AS numbers using sites like ipinfo.io or ipregistry.co we get a match: 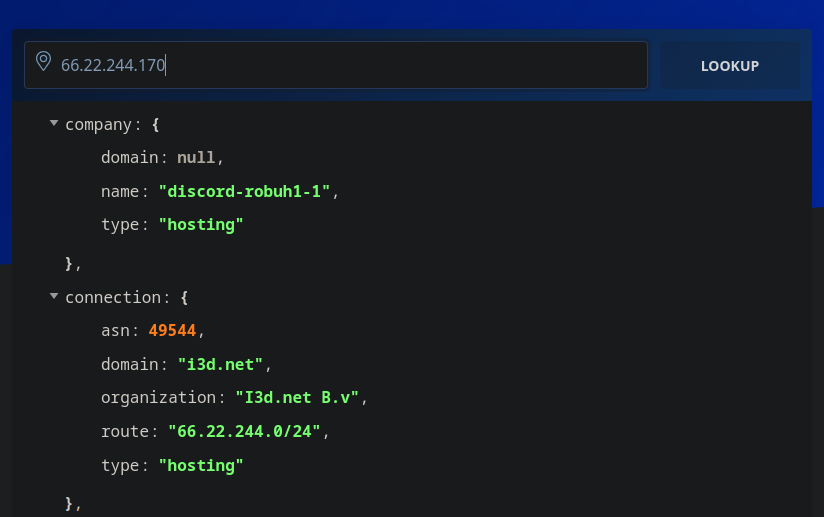 We can see that this IP is in the
We can see that this IP is in the discord-robuh1-1 network, which is operated by i3d.net, which is a "global infrastructure provider, offering low-latency network & solutions to game studios, RTC and enterprises". Checking their advertised networks we can find even more servers:
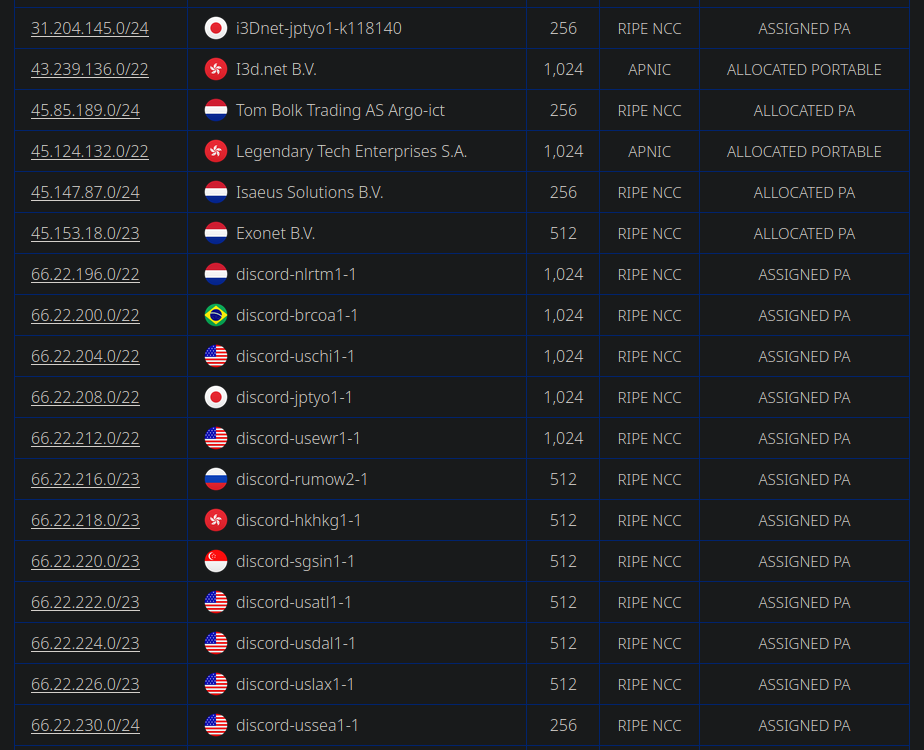
The IPs seem to be in the range of 66.22.192.x - 66.22.248.x which is conveniently almost a full /18 network, so I'm just going to block it all. This is probably fine because if we do other lookups for ranges not shown in the table (but still in the /18 range), we get the "discord" text in the name fields.
DNS replies
We can also try downloading Discord and trying it out (in a VM - obviously) while we are actively monitoring the DNS server's logs.
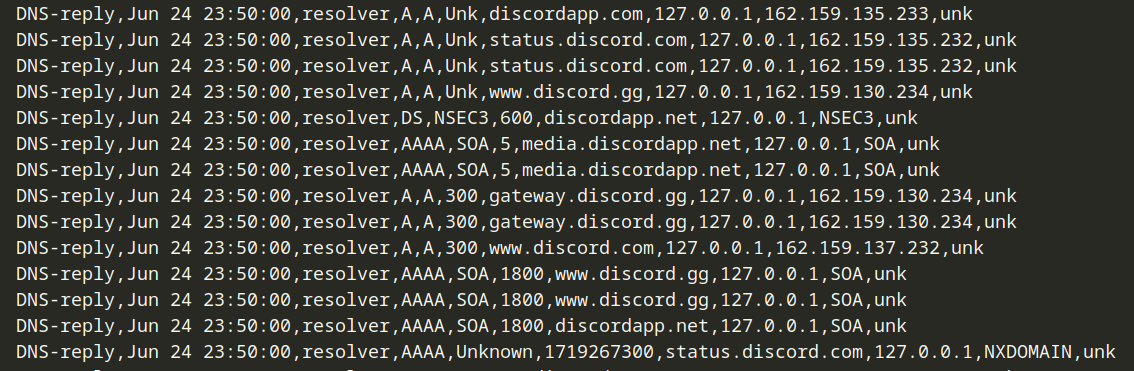 We can extract the domains and create a nice little list.
We can extract the domains and create a nice little list.
Now we have enough information to block the site effectively, so let's set up the firewall rules.
Setting up the firewall
Setting up some aliases for the rules:
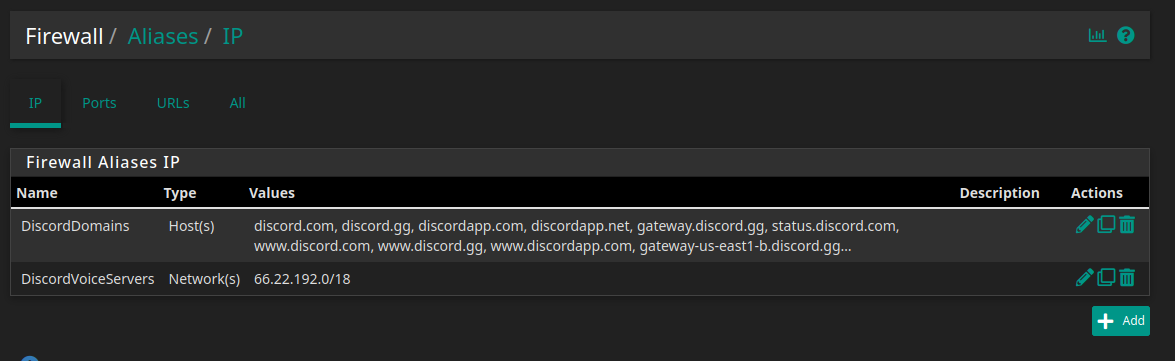
Also I set up some schedules:
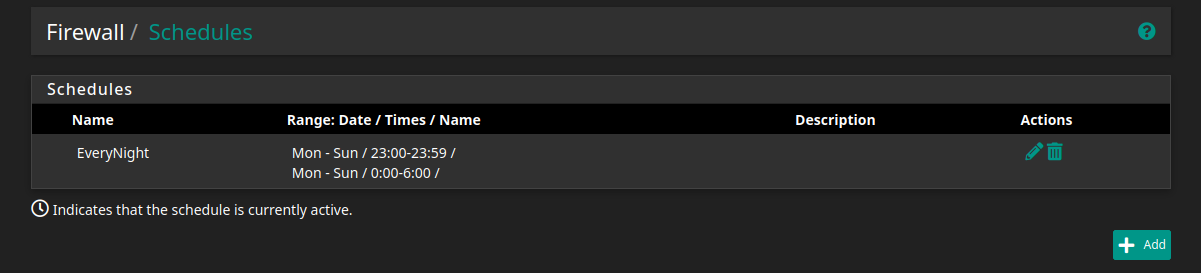 Note: going past 00:00 needs an easy workaround, as seen in the picture.
Note: going past 00:00 needs an easy workaround, as seen in the picture.
And now, the final rules:
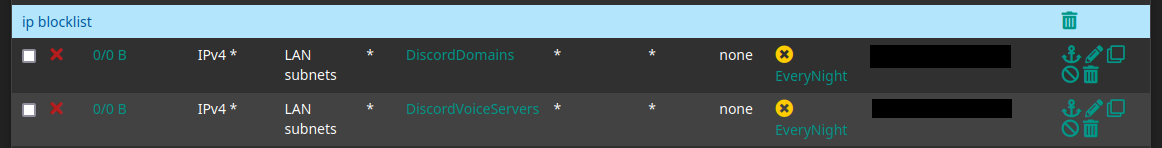 Note: you can set the Schedule field in the Advanced options.
Note: you can set the Schedule field in the Advanced options.
Also, make sure to set "Do not kill connections when schedule expires" under System > Advanced on the Miscellaneous tab.
Limitations
Blocking websites is a cat & mouse game, and clients will always find a way around the restrictions. Because of this, several limitations do exist:
- We may have blocked access for other, unrelated CDNs, which is obviously not ideal
- Clients can use other DNS servers to bypass the DNS blocks
- We can also just block all traffic on port 53 & 853 and allow only our DNS server, which contains these restrictions.
- They can also use DNS over HTTPS, which is tricky to block...
- Clients can use VPNs or proxies to bypass all of this
- We can scrape & ban proxy sites too, but thats not an ellegant solution...
- Clients can use Facebook Messenger, which we are also using, so blocking is not an option
- Except if we narrow down the blocks for certain LAN IP addresses
- But they can request new IPs from the DHCP server
- We can pin their MAC address to the same IP
- They can spoof their MAC, so we would need to maintain a MAC whitelist... who has that much time? Also, modern devices use WiFi MAC address randomization
- Clients can also just talk over the mobile network...
- 4G/5G jammers? Are those even legal?